Workload Identity Federation for ingesting Third party Data into GCS Bucket
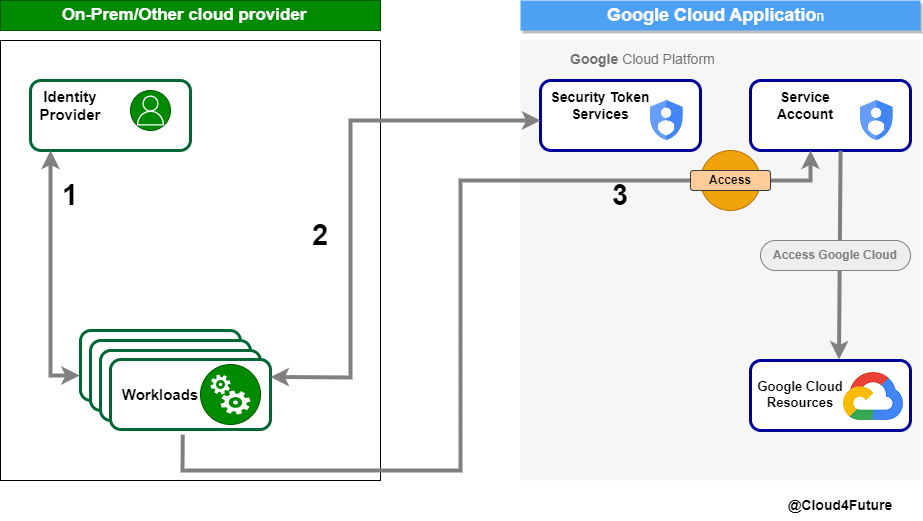
The Google Cloud Platform (GCP) offers Workload Identity Federation, which enables external identities from AWS, Azure, or even OIDC identity providers to be mapped to a Google Cloud service account. With the help of this mapping, external workloads can access Google Cloud services without using service account keys. The workload instead makes use of transient credentials from its native platform or identity provider.
Problem Statement:
The existing system relies on statically controlled service account keys for data input from external sources to our Google Cloud Platform (GCP) storage bucket. Such keys:
require manual rotation and management, which adds to the administrative burden and raises the risk of human error.
They give us access to our GCP resources, so if they are compromised or improperly managed, they could represent a security vulnerability.
Do not offer a centralised means to enforce security regulations across the entire organisation or to keep track of who is using our GCP resources and for what purposes.
As operations become more complex and regulatory requirements become more stringent, using static keys becomes unworkable and dangerous.
Solution Statement:
The aforementioned issues are resolved by implementing Workload Identity Federation, which also provides a scalable, secure, and effective method for data intake from outside sources into a GCP storage bucket.
Workload Identity Federation:
Elimination of Static Keys: Instead of using long-lived static service account keys, we can authenticate external workloads using short-lived credentials from trusted third-party identity providers.
Scalability: This approach scales seamlessly as the number of third-party sources grows, without increasing administrative complexity.
Enhanced Security: By relying on trusted third-party identity providers, we can enforce consistent security policies across all data ingestion operations, ensuring that only legitimate and compliant workloads can ingest data.
Audit and Monitoring: Integrating with external identity providers also provides enhanced audit capabilities, allowing us to monitor and log who is accessing our GCP resources, when, and for what purpose.
Reduced Administrative Overhead: Automating the authentication process reduces the time and effort required to manage and rotate service account keys manually.
Flexibility: Workload Identity Federation supports various identity providers, providing flexibility in terms of integrating with different third-party systems and ensuring consistent authentication mechanisms.
Conclusion
Establishing Workload Identity Federation will improve security, lower administrative burden, improve audit capabilities, and scale effectively with our expanding operations. It will be used to ingestion of data from third-party sources into our GCP storage bucket.
